1Spatial Management Suite is a secured system using an LDAP server to provide the authentication. The services that make up 1Spatial Management Suite need to connect to the LDAP server using authentication providers.
The authentication providers can be set up directly in WebLogic, however you can also use the 1SMS Installation Wizard.
Note: In order to install 1SMS in an environment secured by SSL, you must ensure that the server's certificate(s) are added to the cacerts trust store for the Java version used when WebLogic was installed. This may not be the same as the Java version that is running the installer or the Java running the WebLogic domain. If you are unsure which Java this will be, check the commEnv script found in the oracle_common\common\bin directory in the WebLogic installation.
The settings below are standard settings required to access an LDAP server. Please consult with your IT department for details of your organisation's LDAP server.
![]() Set up authentication Providers
Set up authentication Providers
-
Launch the Installation Wizard.
-
On the Wizard Options screen, select Authentication Provider Setup and click Next to proceed.
-
On the WebLogic Authentication Provider Setup screen, select your type of LDAP server from the LDAP Provider Type drop-down list. By default, this is set to Active Directory.
Click Next to proceed.
-
Enter all required parameters (see Authentication Provider Setup Parameters ).
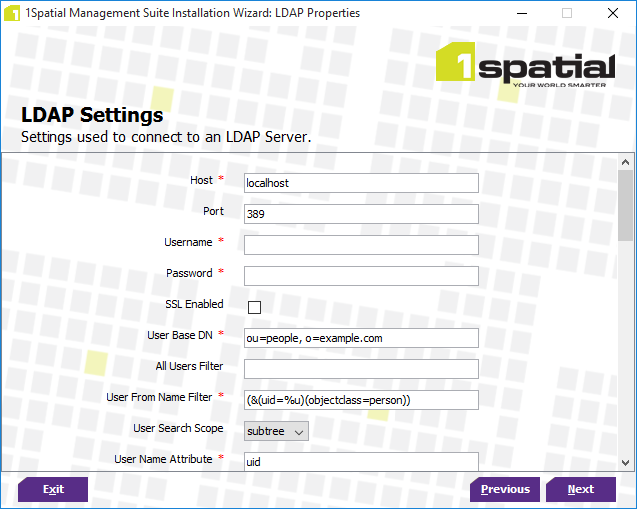
LDAP Settings configuration page
-
Click Next to proceed.
The Installed Servers page is displayed.
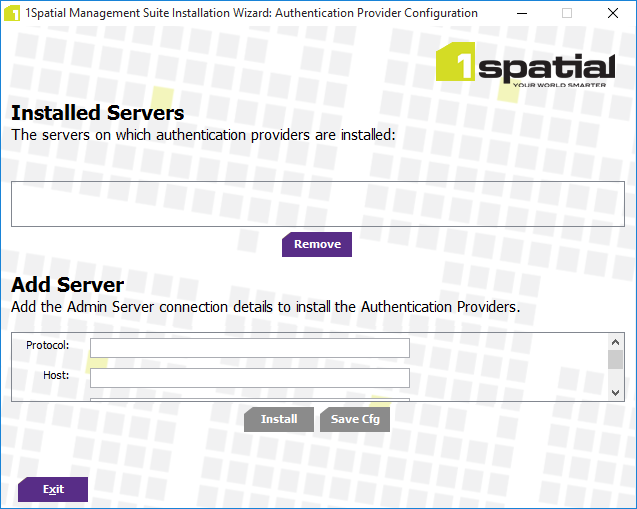
Installed Servers configuration page
-
Enter information for each server in the Add Server area:
-
Protocol - The protocol used for the server (choose "t3" for unsecured, or "t3s" for secured)
Note: If you are using a secured t3s connection, ensure you have installed the certificate in the cacerts trust store for the Java version used to run the installer (as well as the cacerts trust store for the Java version used when WebLogic was installed).
-
Host - The domain host
-
Port - The WebLogic application server port
-
Username - The WebLogic administrator username
-
Password - The WebLogic administrator password
Click Save Cfg to save the configuration for later use, or click Install to add the server to the list of installer servers.
-
-
After setting up the authentication servers, manually restart the WebLogic administration server for each domain and then click Exit to exit the installer.
![]() Authentication Provider Setup Parameters
Authentication Provider Setup Parameters
Note: Ensure that the groups filter returns a reasonable amount of groups. For very large organisations or organisations who are part of a larger LDAP directory, a suitable filter will ensure that only relevant groups are listed. If there are many groups in your LDAP system then ask your IT department (or search online for LDAP filter definitions) for help with defining the groups filter.
| Item | Description | Default Value |
|---|---|---|
| Host | The host name or IP address of the LDAP server. | localhost |
| Port | The port on which LDAP server is listening. | 389 |
| Username | The Distinguished Name (DN) of the LDAP user to connect to the WebLogic server. | |
| Password | The password to connect to the LDAP server. | |
| SSL Enabled | Tick this option if SSL protocol should be used to connect to the LDAP server. | Off |
| User Base DN | The base Distinguished Name (DN) of the tree in the LDAP directory that contains users. | ou=people, o=example.com |
| All Users Filter | If the user object class attribute is not specified, a default search filter is created based on the user schema. | Left blank |
| User From Name Filter | If the user object class and user name attributes are not specified, a default search filter is created based on the user schema. | (&(uid=%u) (objectclass= person)) |
| User Search Scope | Specifies how deep in the LDAP directory tree the LDAP authentication provider should search for users. | subtree |
| User Name Attribute | The attribute of an LDAP user object that specifies the name of the user. | uid |
| User Object Class | The LDAP object class that stores users. | person |
| Use Retrieved User Name As Principal | Specifies whether or not the user name retrieved from the LDAP server should be used as the Principal in the Subject. | Off |
| Group Base DN | The base Distinguished Name (DN) of the tree in the LDAP directory that contains groups. | ou=groups, o=example.com |
| All Groups Filter | An LDAP search filter for finding all groups beneath the base group Distinguished Name (DN.) If the attribute is not specified (that is, if the attribute is null or empty), a default search filter is created based on the Group schema. | Left Blank |
| Group From Name Filter | An LDAP search filter for finding a group given the name of the group. If the attribute is not specified (that is, if the attribute is null or empty), a default search filter is created based on the group schema. | (&(cn=%g) (objectclass= groupofunique names)) |
| Group Search Scope | Specifies how deep in the LDAP directory tree to search for groups. Valid values are subtree and onelevel. | subtree |
| Group Membership Searching | Specifies if group searches into nested groups are unlimited or limited. Valid values are unlimited and limited. | unlimited |
| Max Group Membership Search Level | Specifies how many levels of group membership can be searched. This setting is only valid if GroupMembershipSearching is set to limited. Valid values are 0 and positive integers. For example, 0 indicates only direct group memberships will be found and a positive number indicates the number of levels to search. | 0 |
| Ignore Duplicate Membership | Determines whether or not duplicate members are ignored when adding groups. The attribute cycles in the Group membership. | Off |
| Static Group Name Attribute | The attribute of a static LDAP group object that specifies the name of the group. | cn |
| Static Group Object Class | The name of the LDAP object class that stores static groups. | groupofuniquenames |
| Static Member DN Attribute | The attribute of a static LDAP group object that specifies the Distinguished Names (DNs) of the members of the group. | uniquemember |
| Static Group DNs from Member DN Filter | An LDAP search filter that, given the Distinguished Name (DN) of a member of a group, returns the DNs of the static LDAP groups that contain that member. If the attribute is not specified (that is, if the attribute is null or empty), a default search filter is created based on the group schema. | (&(unique member=%M) (objectclass= groupofunique names)) |
| Dynamic Group Name Attribute | The attribute of a dynamic LDAP group object that specifies the name of the group. | Left blank |
| Dynamic Group Object Class | The LDAP object class that stores dynamic groups. | Left blank |
| Dynamic Member URL Attribute | The attribute of the dynamic LDAP group object that specifies the URLs of the members of the dynamic group. | Left blank |
| User Dynamic Group DN Attribute | If this attribute does not exist, the WebLogic Server determines whether or not a user is a member of a group by evaluating the URLs on the dynamic group. If a group contains other groups, the WebLogic Server evaluates the URLs on any of the descendants (indicates parent relationship) of the group. | Left blank |
| Connection Pool Size | The LDAP connection pool size. | 6 |
| Connection Timeout | The maximum time in seconds to wait for the connection to the LDAP server to be established. If this attribute is set to 0, there is not a maximum time limit. | 0 |
| Connection Retry Limit | Specifies the number of times to attempt to connect to the LDAP server if the initial connection failed. | 1 |
| Parallel Connect Delay | The delay in seconds when making concurrent attempts to connect to multiple LDAP servers. | 0 |
| Results Time Limit | The maximum number of milliseconds for the LDAP server to wait for results before timing out. If this attribute is set to 0, there is no maximum time limit. | 0 |
| Keep Alive Enabled | Specifies whether to prevent LDAP connections from timing out. | Off |
| Follow Referrals | Specifies that a search for a user or group within the LDAP authentication provider follows referrals to other LDAP servers or branches within the LDAP directory. By default, this attribute is enabled. | On |
| Bind Anonymously On Referrals | By default, the LDAP authentication provider uses the same DN and password used to connect to the LDAP server when following referrals during a search. Enable this attribute to connect as an anonymous user. | Off |
| Propagate Cause For Login Exceptions | Specifies whether or not the providers propagate the cause of the LoginException. | Off |
| Cache Enabled | Specifies whether or not a cache is used with the LDAP server. | On |
| Cache Size | The size of the cache (in kilobytes) that is used with the LDAP server. | 32 |
| Cache TTL | The time-to-live of the cache (in seconds) that is used with the LDAP server. | 60 |
| Guid Attribute | Specifies the name of the GUID attribute defined in the LDAP server that corresponds to the LDAP Authentication provider configured in the security realm. |
