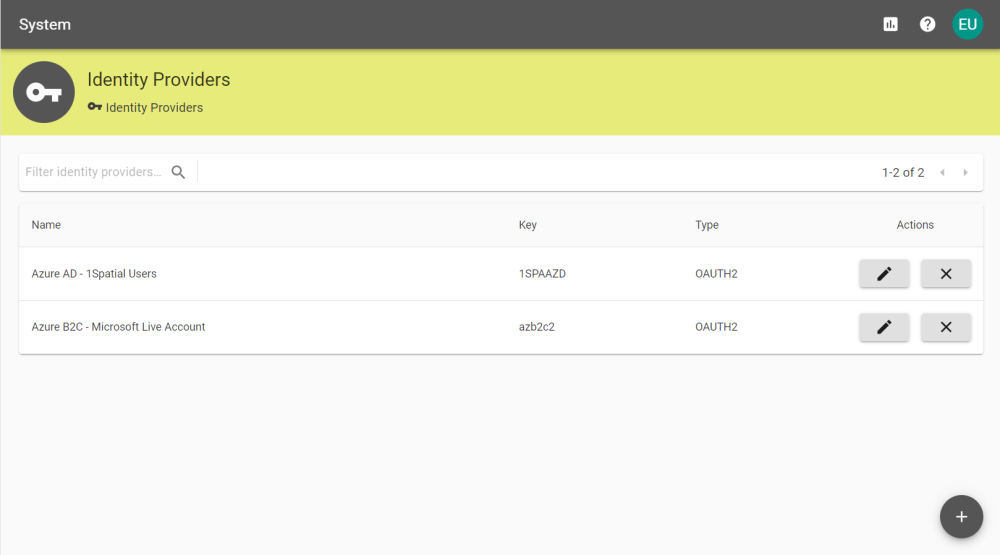
Identity Providers
The Identity Providers page can be reached by an Administrator via the Identity Providers section in the System tab.
User authentication can be provided from a SAML or OAuth based Identity Provider.
Note: In order to use this method of authentication users must have been created ahead of time, unless Create missing users on login? is set in the Identity Provider Settings. For information on adding individual users manually visit the Users, or for bulk creation, the User Import section.
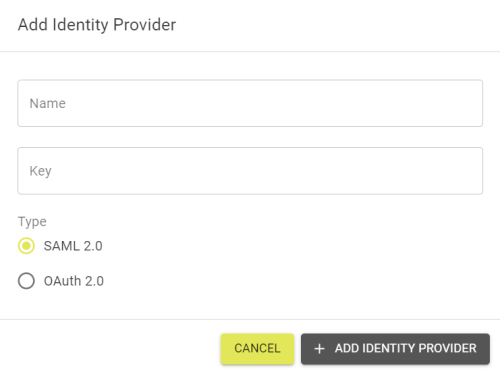
To add a new Identity Provider click the ![]() button and enter a Name and Key for the provider, and choose the authentication type.
button and enter a Name and Key for the provider, and choose the authentication type.
These providers will be listed on the 1Data Gateway login screen above the Sign in with username/password option.

 Configuring SAML 2.0
Configuring SAML 2.0
After creating a SAML 2.0 provider the following tabs must be configured:
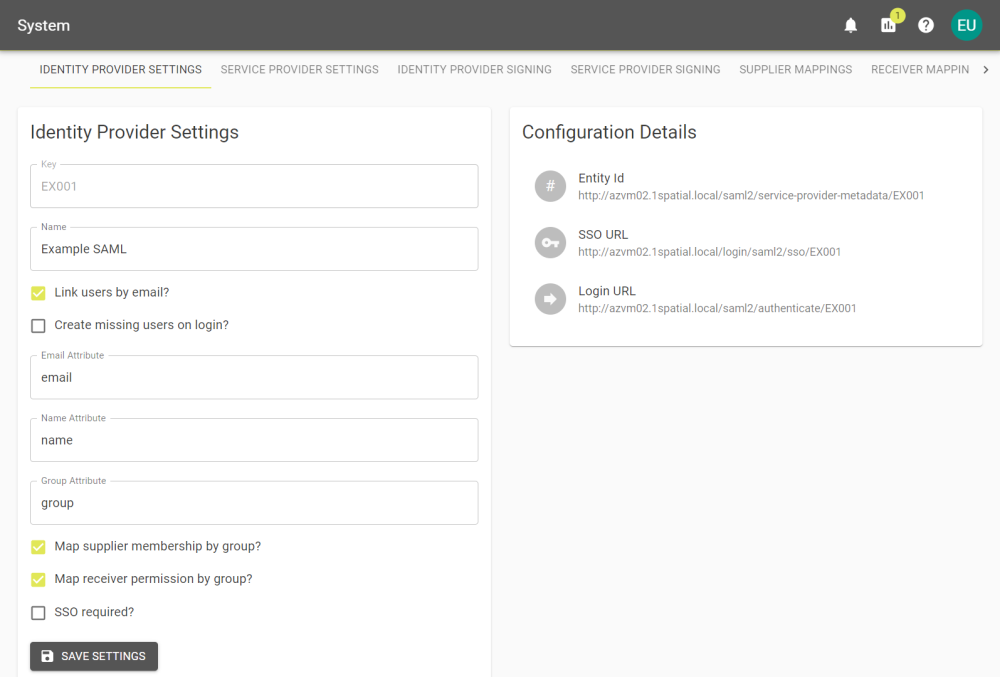
 Identity Provider Settings
Identity Provider Settings
|
Parameter |
Description |
|---|---|
| Name |
Defined when adding the provider, the name you want to give this connection. |
|
Map By Email? |
Select this to map the emails provided by the remote system, to those already provided in your 1Data Gateway installation. Creates identity provider links as users log in. If you do not select Map By Email you will need to configure Identity Provider links manually. See the Users section for more. |
|
Create missing users on login? |
When a User logs in via this Identity Provider, if they do not have a user profile in the system they will have a user profile created. This allows groups to be mapped to Identity Providers, allowing access to be restricted to groups. |
|
Email Attribute |
The name of the attribute that contains emails in your identity provider. |
|
Name Attribute |
The name of the attribute that contains users names in your identity provider. |
|
Group Attribute |
The name of the attribute that contains groups in your identity provider. |
|
Map supplier membership by group |
Enable this to access the Supplier Mappings tab. |
|
Map receiver permission by group |
Enable this to access the Receiver Mappings tab. |
|
SSO required? |
Select to force users to connect to 1Data Gateway through single sign on. If this is set the user accounts linked to the IDP cannot login using a 1DG-local password and must authenticate against the remote system. |
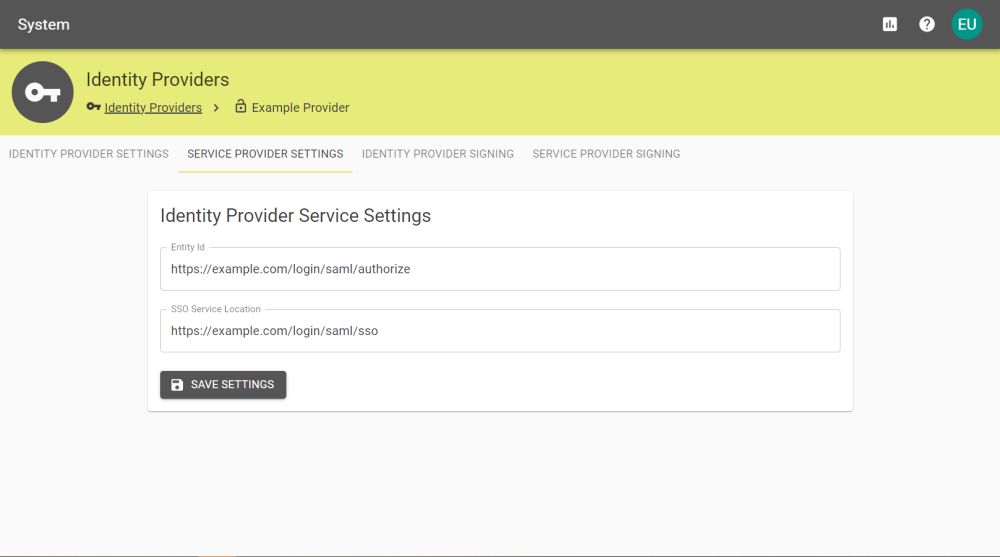
 Service provider Settings
Service provider Settings
|
Parameter |
Description |
|---|---|
|
Entity ID |
The URI location for the Identity Provider you will be using. |
|
SSO Service Location |
The URI location for the Single Sign On service you will be using. |
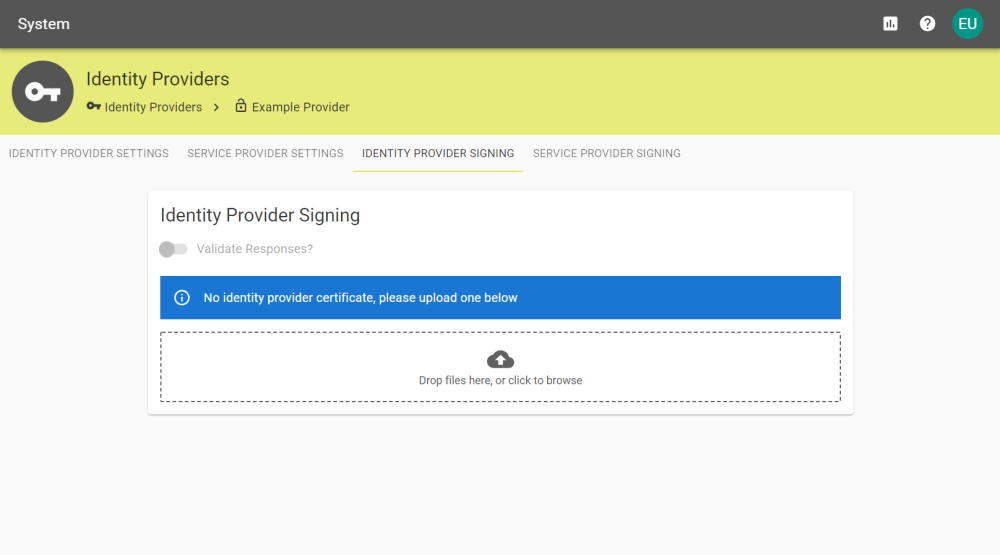
 Identity Provider Signing
Identity Provider Signing
Upload your certificate to this panel, and select validate responses.
Note: The certificate presented must be a PEM file.
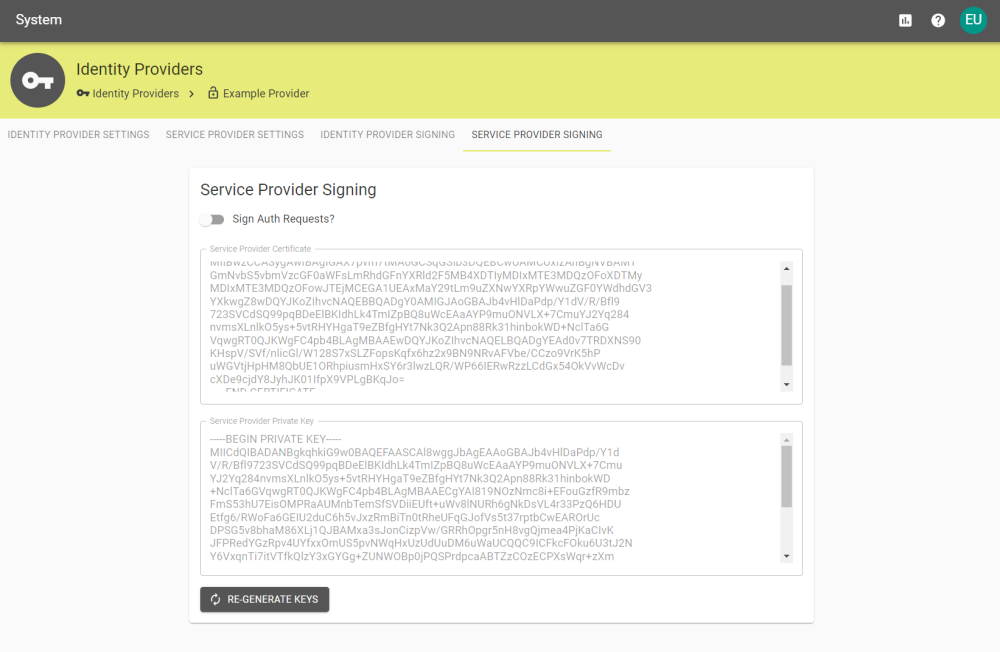
 Service Provider Signing
Service Provider Signing
|
Parameter |
Description |
|---|---|
|
Sign Auth Requests? |
Select to enable the signing of Authorization Requests. |
|
Service Provider Certificate |
The generated service provider certificate. |
|
Service Provider Private Key |
The generated service provider private key. |
 Supplier Mapping
Supplier Mapping
After enabling and saving Map supplier membership by group in the Identity Provider Settings tab, the Supplier Mapping tab will appear.
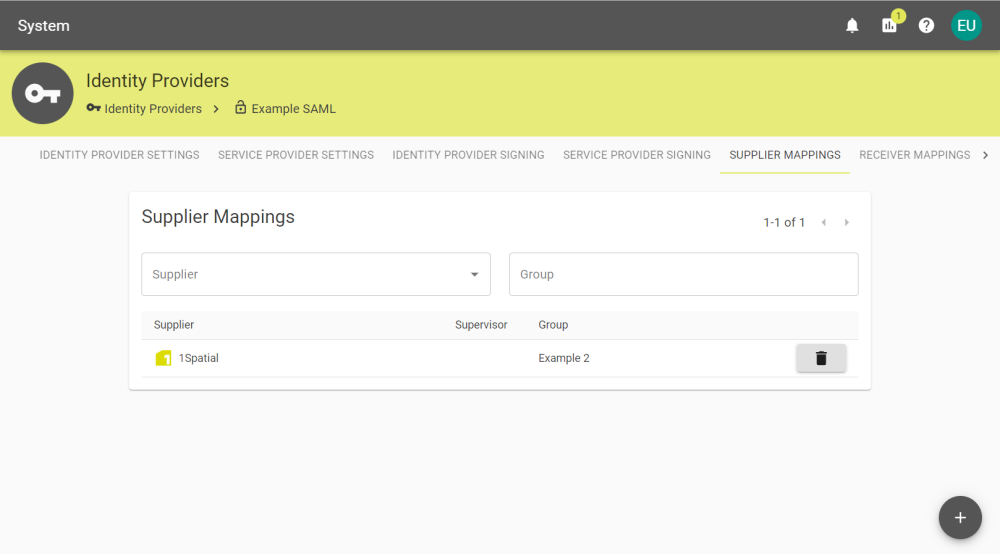
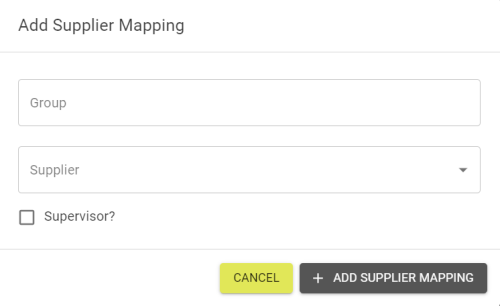
You can create mappings that automatically add users to a supplier based on groups by clicking the ![]() button and entering the group.
button and entering the group.
Mappings can be deleted by clicking the ![]() button and confirming deletion.
button and confirming deletion.
 Receiver Mapping
Receiver Mapping
After enabling and saving Map receiver permissions by group in the Identity Provider Settings tab, the Receiver Mapping tab will appear.
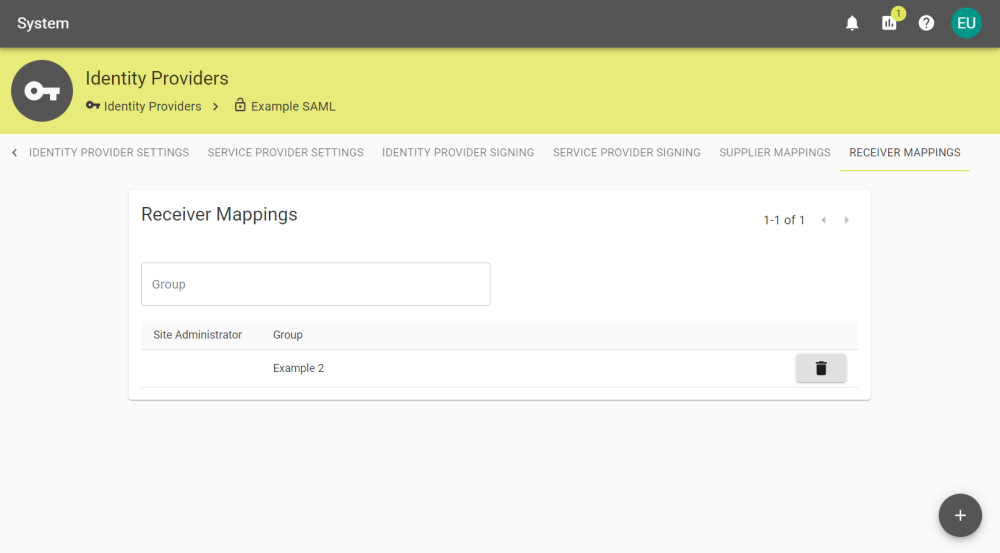
You can create receiver permissions that automatically apply to Users within the specified group by clicking the ![]() button and entering the group.
button and entering the group.
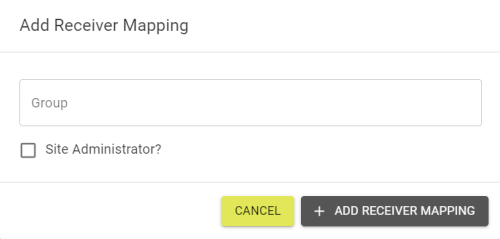
Mappings can be deleted by clicking the ![]() button and confirming deletion.
button and confirming deletion.
 Configuring OAuth 2.0
Configuring OAuth 2.0
After creating a OAuth 2.0 provider the following tabs must be configured:
For detailed information OAuth configuration, please refer to the OAuth documentation.
 Identify Provider Settings
Identify Provider Settings
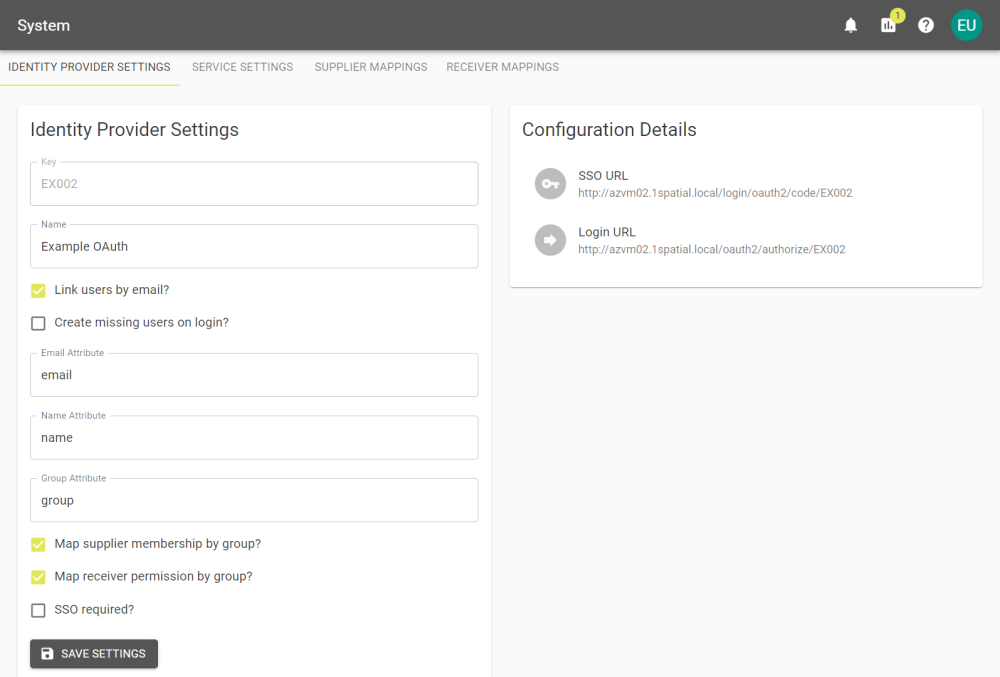
|
Parameter |
Description |
|---|---|
|
Name |
Defined when adding the provider, the name you want to give this connection. |
|
Map By Email? |
Select this to map the emails provided by the remote system, to those already provided in your 1Data Gateway installation. Creates identity provider links as users log in. If you do not select Map By Email you will need to configure Users. See the Identity Providers section for more. |
|
Create missing users on login? |
When a User logs in via this Identity Provider, if they do not have a user profile in the system they will have a user profile created. This allows groups to be mapped to Identity Providers, allowing access to be restricted to groups. |
|
Email Attribute |
The name of the attribute that contains emails in your identity provider. |
|
Name Attribute |
The name of the attribute that contains users names in your identity provider. |
|
Group Attribute |
The name of the attribute that contains groups in your identity provider. |
|
Map supplier membership by group |
Enable this to access the Supplier Mappings tab. |
|
Map receiver permission by group |
Enable this to access the Receiver Mappings tab. |
|
SSO required? |
Select to force users to connect to 1Data Gateway through single sign on. Note: If this is set, the user accounts linked to the IDP cannot login using a 1Data Gateway local password and must authenticate against the remote system. |
 Service Settings
Service Settings
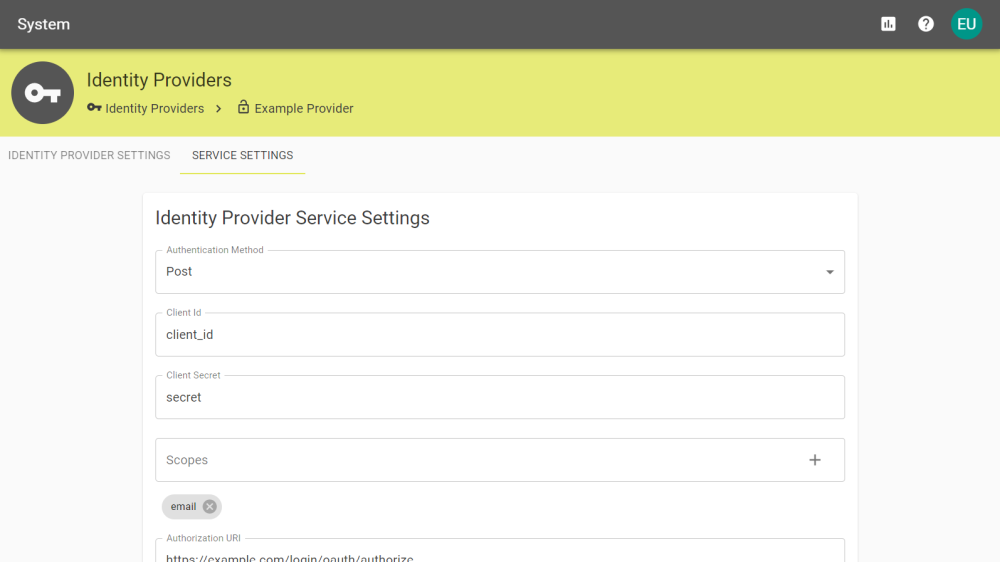
|
Parameter |
Description |
|---|---|
|
Authentication Method |
Select which method should be used to make the User Info request. |
|
Client Id |
The client Id associated with the OAuth registration. |
|
Client Secret |
The client secret associated with the OAuth registration. |
|
Scopes |
Define the scope to limit access to specific values in the users account. e.g: email Note: The name of these values will change depending on the values within your setup. |
|
Authorization URI |
The location of the authorization token for the OAuth connection. |
|
Token URI |
The location of the OAuth token. |
|
Jwk set URI |
The location of a JSON Web Key used for authentication. |
|
User Info URI |
The location of the users information where the tokens are sent. |
|
User Name Attribute Name |
The name of the attribute in your authentication provider configuration that stores the Users names. |
|
User Info Authentication Method |
What method should be used to make the Authentication request. |
 Supplier Mapping
Supplier Mapping
After enabling and saving Map supplier membership by group in the Identity Provider Settings tab, the Supplier Mapping tab will appear.
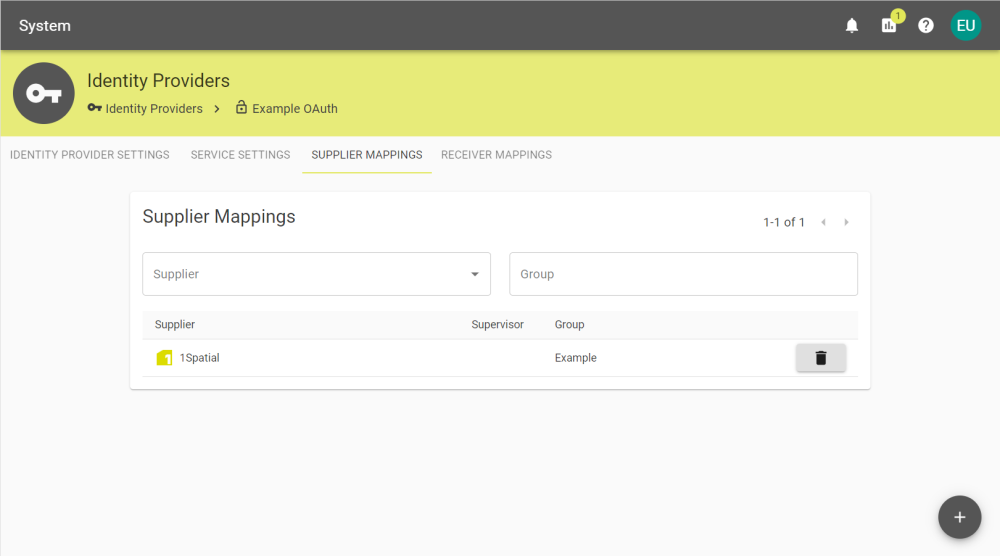
You can create mappings that automatically add users to a supplier based on groups by clicking the ![]() button and entering the group.
button and entering the group.

Mappings can be deleted by clicking the ![]() button and confirming deletion.
button and confirming deletion.
 Receiver Mapping
Receiver Mapping
After enabling and saving Map receiver permissions by group in the Identity Provider Settings tab, the Receiver Mapping tab will appear.
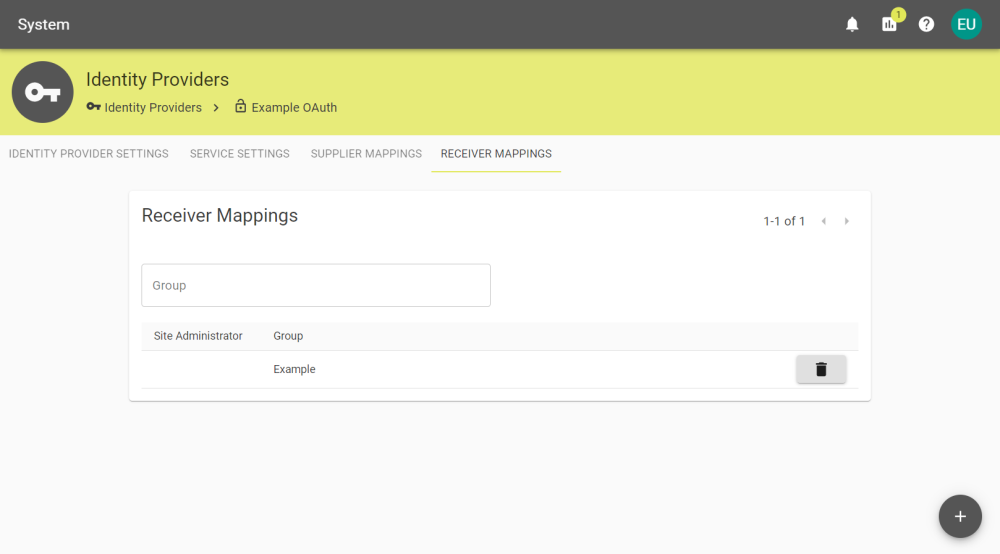
You can create receiver permissions that automatically apply to Users within the specified group by clicking the ![]() button and entering the group.
button and entering the group.

Mappings can be deleted by clicking the ![]() button and confirming deletion.
button and confirming deletion.